Our web intelligence platform indexes and assesses hundreds of websites per day, looking for high-severity vulnerabilities that can result in data exposure or data loss - a "user"-allied activity. Earlier this week, we autonomously detected exposed or leaking data during a routine surface scan on sjsm.org.
Further investigation led us to index data from, and now disclose, a prior undisclosed breach that St. James Medical School did not seem to communicate to consumers or students about.
For those of you expecting fancy forensic examples, be aware - this is a multi-year-old leak/breach just now being discovered - not a fresh IR case. While the breach matter is real, due to the length of time that's passed this is, at this point, theatrical storytelling.
So, here goes.
Saint James School of Medicine is a private for-profit offshore medical school with two basic science campuses, one in British Overseas Territory of Anguilla, and the other in Saint Vincent and the Grenadines, it is considered one school with two campuses.
Within their internal systems, they provide multiple resources for students to interact with and communicate through - a set of student forums being one of these said resources.
Tuesday, November 30, 2021 8:56:16 AM, a threat actor using the moniker "Moki" and the Google account "jatordmoki@gmail.com" accessed the Saint James School of Medicine Student Forums from the IP address "98.30.61.154" and created a series of posts stating...
Hi my name is Moki. The university has been hacked and all the information of students and doctors has been stolen. Not only site information but all information inside the university computers is for sale
This was repeated 18+ different times, including...
- Tuesday, November 30, 2021 9:03:12 AM
- Tuesday, November 30, 2021 9:03:55 AM
- Tuesday, November 30, 2021 9:05:20 AM
- Tuesday, November 30, 2021 9:07:14 AM
- Tuesday, November 30, 2021 9:07:41 AM
- Tuesday, November 30, 2021 9:07:58 AM
- Tuesday, November 30, 2021 9:08:20 AM
- Tuesday, November 30, 2021 9:08:59 AM
- Tuesday, November 30, 2021 9:09:16 AM
- Tuesday, November 30, 2021 9:10:12 AM
- Tuesday, November 30, 2021 9:10:38 AM
- Tuesday, November 30, 2021 9:10:59 AM
- Tuesday, November 30, 2021 9:11:18 AM
Assuming "Moki" wasn't lying - 2/3 years post-infection/post-exploitation, there's no shot at finding out what precisely happened here. We don't know. We could have found out then. There's no chance at figuring that out clearly now.
Regardless of if "Moki" was telling the truth or not, the claims started a chain reaction that leads to December 18th, 2021 - about two weeks later. Whether through exploitation by "Moki" or during an IT Department response to the issue, a mySQL dump containing the forum and user data was saved to the disk.
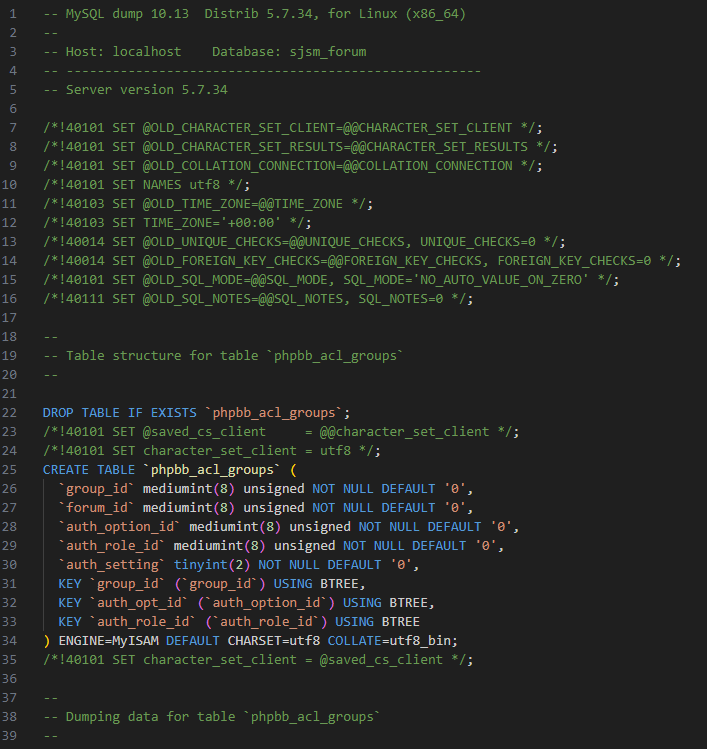
This dumped SQL file was subsequently compressed into an archive, then moved and left on an open, "served" directory with no access controls, password protection, or guardrails in general.
We don't know for how long it was "publicly exposed". There is no way to sensibly compute the interim security of the file prior to us finding it. We detected this on February 19th and contacted Saint James on February 20th, here we are publishing this February 21st.
Contained within the SQL file is a whole, temporally set copy of the following data:
- User IP Addresses
- User Email Addresses
- User Forum Posts and Replies that include self-disclosed PI
- User Forum Attachments
- Forum Logs
- Debug Logs
- and more related and unrelated equally
All following the lifespan of the forums pre-2021.
What happens now?
We disclosed a copy of the database dump privately to Troy Hunt from HaveIBeenPwned for indexing and disclosure. We looked for any data breaches or incidents disclosed by Saint James around this time and found nothing newsworthy.
Whether it was or wasn't a legitimate breach back in 2021, it is technically now at this point considering the access control failures. We'll give Troy & HIBP a typical "30 days" to decide whether they wish to do a writeup, notifications, etc, or not index it at all - their choice - then we'll share it here so that it is indeed, to the bone, a "breach" - also for other orgs to add to their own breach trackers if needed.
We caution educational institutions against "making the budget work". If you need more coverage, more software, more checks, more of whatever it is you need - you will still need it even after the breach occurs. Low, spotty, or nonexistent security coverage of what's building futures for others, is the wrong way to do it.